 Software Enhancement Modules (SEMs) unlock advanced features within CyberAudit software that provide specific functionality. Each SEM can be purchased individually, enabling CyberAudit customers to pay for only the features they need.
Software Enhancement Modules (SEMs) unlock advanced features within CyberAudit software that provide specific functionality. Each SEM can be purchased individually, enabling CyberAudit customers to pay for only the features they need.
Compatible software versions:
= Basic | = Enterprise
Maps and Location Graphics Module (CAW-M01)
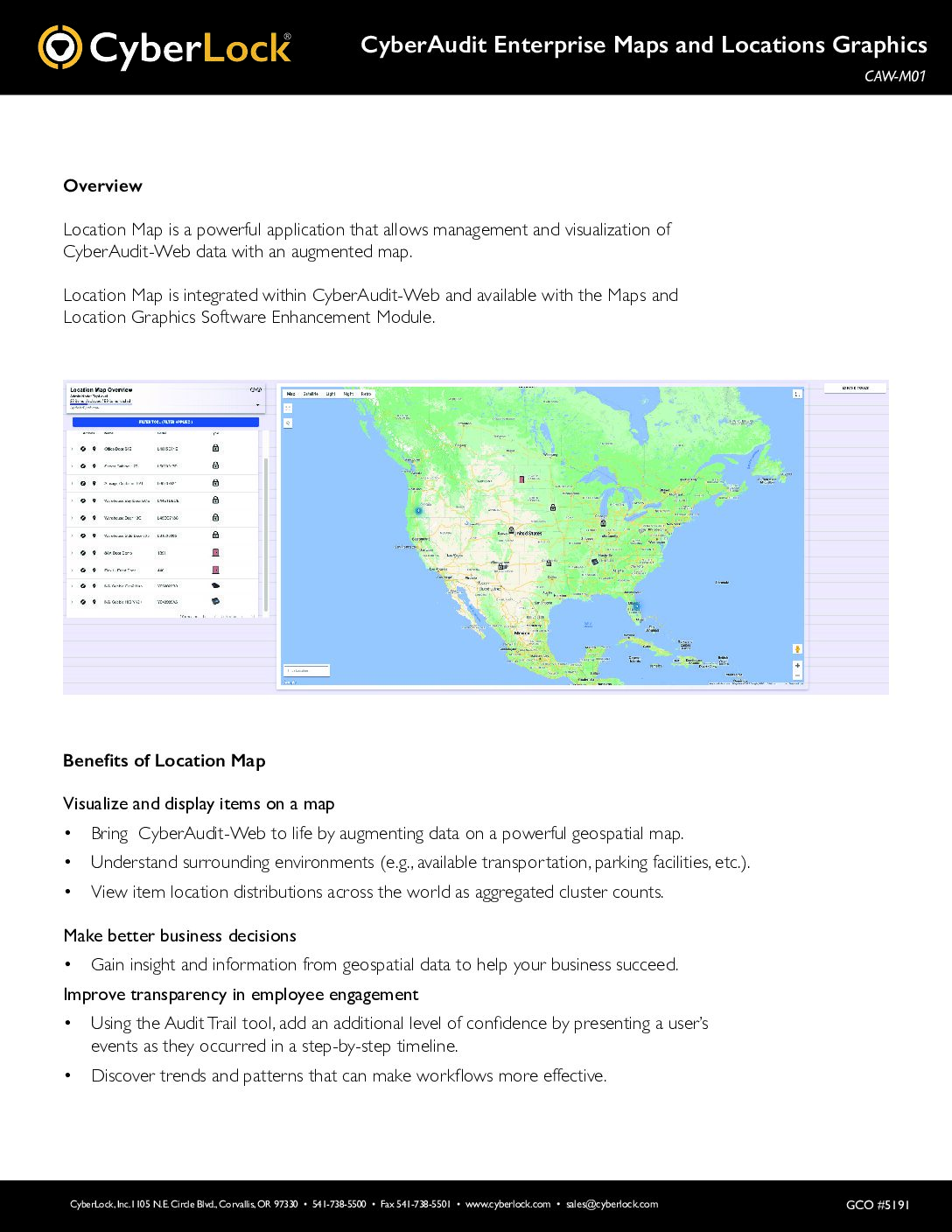 The Maps and Location Graphics module allows you to manage and visualize your CyberAudit-Web data with Google Maps. It also opens a visual interface tool that allows CyberLocks and Communicators to be graphically “placed” on the drawings, pictures, or maps (JPEG or PNG). In particular, this model helps large and geographically spread-out CyberLock deployments improve tracking and locating of locks and communicators. Geographic coordinates enable exporting data to many GIZ systems to create CyberLock system layers.
The Maps and Location Graphics module allows you to manage and visualize your CyberAudit-Web data with Google Maps. It also opens a visual interface tool that allows CyberLocks and Communicators to be graphically “placed” on the drawings, pictures, or maps (JPEG or PNG). In particular, this model helps large and geographically spread-out CyberLock deployments improve tracking and locating of locks and communicators. Geographic coordinates enable exporting data to many GIZ systems to create CyberLock system layers.
Door Support Module (CAW-M02)
 The Door Support software module adds software features required to manage all the functionality the Door & I/O hardware module brings to a Flex System installation. In addition to managing individual access rights to each door, Request-to-Exit (RTE) events are recorded, doors can be set to automatically unlock and relock at specified times, door sensors are monitored, and alarms can be triggered if a door is forced or left open after a specified amount of time.
The Door Support software module adds software features required to manage all the functionality the Door & I/O hardware module brings to a Flex System installation. In addition to managing individual access rights to each door, Request-to-Exit (RTE) events are recorded, doors can be set to automatically unlock and relock at specified times, door sensors are monitored, and alarms can be triggered if a door is forced or left open after a specified amount of time.
Advanced Security Features Module* (CAW-M03)
The Advanced Security Features Module includes three security features. The first is an option that makes the first key of a multi-key operation the sole key able to open a CyberLock cylinder within an eight-second window. The second adds a Temporary Activation option that enables activating an expired CyberKey smart key for five minutes by touching a selected CyberLock cylinder or CyberPoint electronic tag. The third feature provides an option to limit Temporary Activation and One-Time Use settings to an 8-second window. Enables the use of TOTP Two-Factor Authentication for a higher level of login security for administrators.
*For CAW versions 9.8 or older. Advanced Security Features are standard in current CAW versions.
Lock List Expansion (CAW-M04)
The Lock List Expansion module enables limiting the number of locks loaded into CyberKey smart keys on a per communicator basis. This is needed when CyberKey smart keys require individual permission to more than the maximum 3300 locks they can now hold. With this enhancement, keys and missions may be granted access to an overall unlimited number of individual CyberLock cylinders and each communicator in the system filters the locks to selected tags.
Active Directory / Azure AD (CAW-M05)
The Active Directory/Azure AD synchronization module enables synchronizing selected security groups and users from Microsoft Active Directory® or Azure® AD to people tags and people in a CyberAudit-Web system. The users and groups become ‘linked’ records.
CyberAudit-Web synchronizes with its designated Active Directory daily or on-demand to add, update, or remove groups and users. A set of user attributes may be mapped to fields in People records.
‘Linked’ people may be designated as system administrators. Their login password is verified against their Active Directory or Azure AD password.
Advanced Door Features (CAW-M06)
The Advanced Door Features module adds three features to use with doors:
- A No PIN required schedule – During this time a person with a PIN will not be required to enter their PIN to gain access to the door. This would be useful in a case where a PIN is not required during normal business hours but would be required outside of that time.
- Keep Unlocked Calendar entries – Allows scheduling times in the future where a door will be held unlocked. CyberAudit-Web adds the time frame of the calendar entry to the door’s keep unlocked schedule in the week of the calendar entry. This feature is useful to managers of facilities that schedule events on a calendar basis and want the door to be held unlocked for those events.
- A door monitor window – Shows door activities in a scrolling window as they occur.
Rolling Access Codes (CAW-M08)
Automates the process of changing lock access codes for some or all CyberLocks in a system. Access codes may be configured to change (roll) occur on a periodic basis. A “grace period” may be designated during which the lock will continue to honor the old access codes to complete the change for all affected locks.
FlashLock Compatibility (CAW-M09)
The FlashLock module adds complete support for adding FlashLocks and fobs to a CyberLock system. To grant access, FlashLocks may be added to an access list . Fobs may be assigned to people and given an expiration rule. Flash access may be distributed by email or text message.
Dynamic Tags Module (CAW-M10)
Dynamic Tags enable granting access to CyberLocks based upon the values of user-defined fields in People, Lock, People tag, and Lock tag records. Unlike the traditional static tags, locks and people are automatically added to and removed from Dynamic Tags based upon whether their user-defined field values match the criteria of the tag.
Dynamic Tags can automatically grant or revoke access when the attributes of a person or lock change. For example, if access to a lock should only be permitted when a person’s safety qualification has not expired, a person’s access to the lock can be automatically revoked on the day the license expires.
Fobs (CAW-M12)
The Fobs module adds support for adding IR fobs to a CyberLock system. Fobs may be assigned to people and given an expiration rule. Fobs can be used to gain access to CyberLock Blue and CyberLock NFC products, as well as doors via a FlashReader.
Dynamic Audit Events/Camera and NVR Integration (CAW-M14)
The Camera and NVR Integration module leverages Frigate NVR and compatible cameras to capture and link video clips with standard CyberAudit-Web audit trails, creating an enhanced record called Dynamic Audit Events. It provides monitoring via live streaming and email notifications with links to video clips.
OSDP Support (CAW-M15)
The OSDP Software Enhancement module enables connecting a third party RFID card reader to a Flex II System controller, a FlexEdge controller, or ValidiKey Vault via the Open Supervised Device Protocol.
